SSL Certificate
Deploy an SSL certificate to enable HTTPS encryption of websites, trusted identity authentication and prevent against data leaks or tampering during transmission.
Get SSL Certificate >Blog > Prevent Email Leakage with S/MIME
Tag:
Email Leakage
S/MIME Certificate
2952:0
CatherineJuly 28 2023

Previously, we have introduced how the digital signature feature of S/MIME certificates helps protect against phishing email attacks. In this article, we will explore another essential function of S/MIME certificates: encryption. By leveraging encryption, S/MIME certificates ensure the confidentiality and integrity of email messages, effectively preventing information leakage and tampering.
In addition to phishing email attacks, there have been numerous incidents of email leaks, with notable examples such as the leaked emails of Hillary Clinton and the Beckhamgate. Email content can be compromised in a lot ways, such as falling victim to phishing emails, having accounts hijacked, or unauthorized interception during transmission. So, how can we effectively prevent email information leakage?
On the one hand, everyone needs to raise awareness about email security and adopt strong, high-security passwords. On the other hand, employing S/MIME certificates for email encryption offers a powerful solution to prevent email leakage.
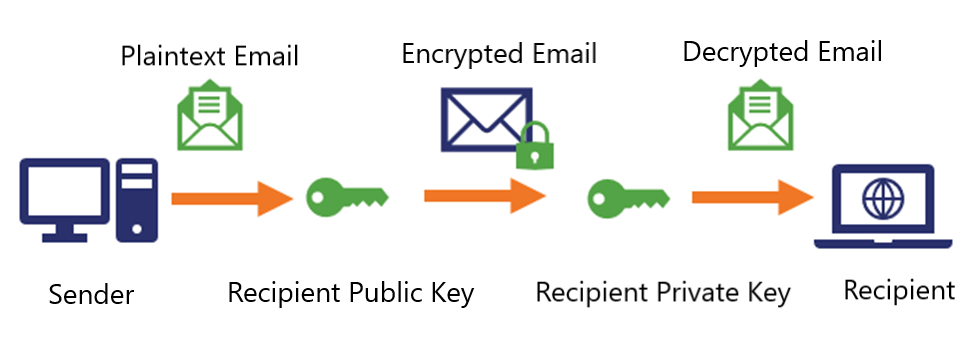
Secure/Multipurpose Internet Mail Extensions (S/MIME) certificates use the S/MIME protocol to provide identity authentication through digital signatures. These certificates ensure that you are a legitimate sender, protecting you from falling victim to phishing attacks. Furthermore, S/MIME certificates utilize asymmetric encryption to encrypt and decrypt email messages. When a sender encrypts a message using the recipient's public key and sends it, the recipient can only decipher and access the content using their corresponding private key. This robust encryption method offers strong protection against interception, eavesdropping, tampering, and unauthorized disclosure of email data.
The figure below illustrates the working principles of S/MIME certificates:
- Visit www.nicsrs.com and log in to your account.
- Select the desired S/MIME certificate to purchase.
- Apply for email validation. For the specific steps, please see below (Sectigo as example). Once the validation process is completed, you will obtain the S/MIME certificate.
1. The application and installation of the S/MIME certificate must be done on the same computer and with the same browser. Windows users should utilize Internet Explorer (version 11 or above), while MAC users should use Firefox.
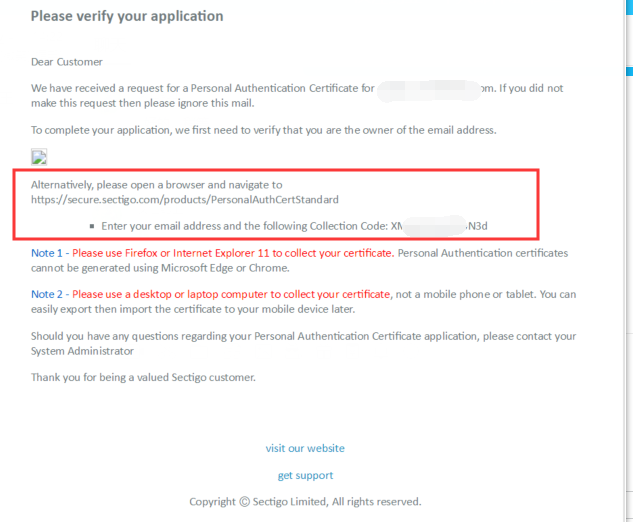
2. After initiating the application process, you will receive an email titled "Verify Your Application." Please use Internet Explorer to open the link provided in the email and enter the verification code enclosed in the email. Refer to the screenshot below for the email content. It is essential not to close the browser or any of the pages opened during the application process, regardless of any other actions taken.
Then, here is the next page. Upon clicking the button on the page, a confirmation message will appear. Click "Yes" to proceed. (In case you accidentally click "No," simply click the "Request My Certificate Now" button again, followed by clicking "Yes.")

3. After completing the aforementioned steps, you’ll see this page, as shown below. Don’t close this page and wait for 5 to 10 minutes. During this period, the certificate will automatically install successfully. The page may automatically refresh and redirect to sectigo.com, but do not interact with it.

4. After approximately 5 minutes or upon receiving an email titled "Your certificate is ready for collection," your certificate has been installed successfully. At this point, you can check whether the installation was successful by navigating to: Tools -> Internet Options -> Content -> Certificates -> Personal.
5. Finally, refer to the process on the pages below to export the certificate, public key, and private key.
Windows: https://support.sectigo.com/Com_KnowledgeDetailPage?Id=kA01N000000zFK0
Mac: https://support.sectigo.com/Com_KnowledgeDetailPage?Id=kA01N000000zFK2
RELATED
2025-12-18 15:37:42
2025-12-17 18:03:54
2025-11-27 13:34:03
2025-10-16 11:03:19
2025-09-23 15:00:41
Categories

Free SSL Tools
Top Posts
Comments