SSL Certificate
Deploy an SSL certificate to enable HTTPS encryption of websites, trusted identity authentication and prevent against data leaks or tampering during transmission.
Get SSL Certificate >Blog > The Art of Deception: Unveiling Brand Impersonation
Tag:
Brand Impersonation
SSL Certificate
Email Signing Certificate
2907:0
CatherineMay 23 2023

Email remains one of the primary channels in both personal and business communication. Unfortunately, this convenience comes with its fair share of risks, including brand impersonation. Brand impersonation through email refers to cybercriminals masquerading as legitimate brands to deceive recipients, gain their trust, and exploit sensitive information or commit fraud. In this article, we will talk about brand impersonation, what is it, and the potential consequences and some measures you should take to defend against this type of cyberattack.
Brand impersonation refers to the practice of creating deceptive communications or websites that mimic the branding and appearance of legitimate organizations. By leveraging the familiarity and trust associated with well-known brands, cybercriminals aim to deceive individuals into divulging personal data, login credentials, or financial information. Brand impersonation is commonly observed in phishing attacks targeting financial institutions, e-commerce platforms, social media platforms, and popular online services.
Brand impersonation through email involves the fraudulent use of a recognizable brand's name, logo, and email format to trick recipients into believing that the communication is legitimate. Attackers often leverage social engineering techniques to manipulate recipients into taking certain actions, such as clicking on malicious links, providing personal information, or initiating unauthorized transactions.
Phishing Emails
One prevalent form of brand impersonation is phishing emails, where attackers mimic reputable organizations, such as banks, e-commerce platforms, or social media networks. They design emails that closely resemble authentic correspondence, complete with official logos and email templates. These emails often claim urgent account updates, security alerts, or financial transactions that require immediate action. Recipients are then directed to fraudulent websites or asked to provide sensitive information, compromising their security.
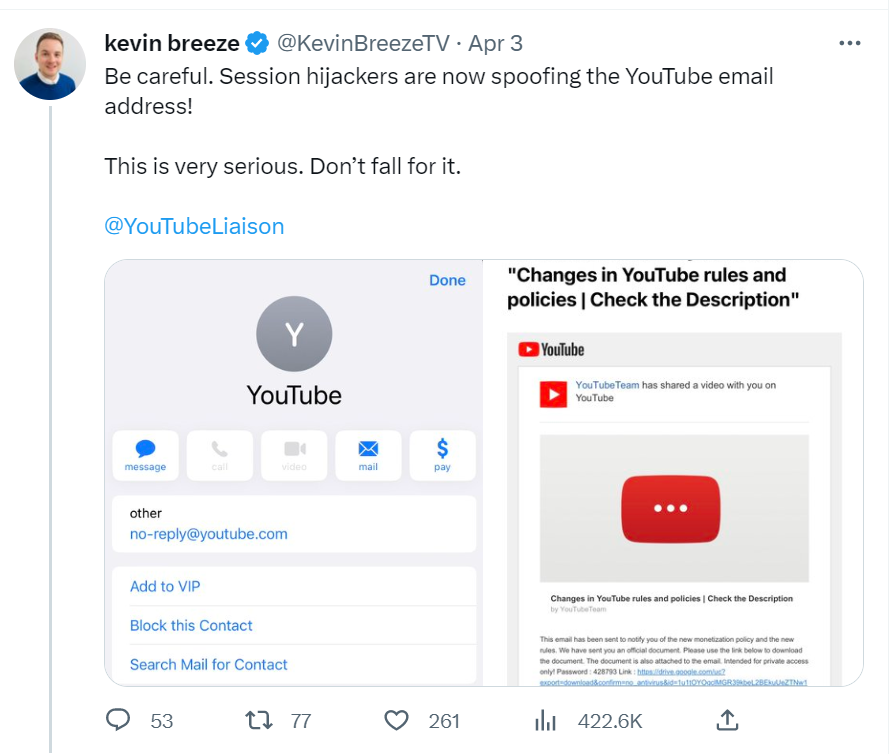
On May 3rd, YouTube creator Kevin Breeze discovered a new phishing scam. He received an email from [email protected]. The content of the letter was that YouTube notified the new policy and also contained a Google Drive link. Users must reply through this link within 7 days, otherwise, the YouTube account will be restricted. In fact, if the user opens the link and enters the required information, their YouTube account will be hijacked. Considering that most YouTube users log in with their Gmail account, if their YouTube accounts are hijacked, their Gmail data will be stolen as well.
The reason this phishing is so difficult to tell is that the scammers deliver the seemingly genuine phishing email through the platform's "Share Video by Email" feature, taking advantage of the official YouTube email address, so It's easy to fall into their trap.
Business Email Compromise (BEC)
BEC attacks target individuals within organizations who have access to sensitive information or the authority to initiate financial transactions. Attackers pose as executives, vendors, or clients and send emails to employees, urging them to transfer funds or disclose sensitive data. These emails are meticulously crafted to imitate the brand's tone, language, and email signatures, tricking recipients into complying with fraudulent requests.
IC3 received a record number of complaints from the American public in 2020: 791,790, with reported losses exceeding $4.1 billion. This represents a 69% increase in total complaints from 2019. Business E-mail Compromise (BEC) schemes continued to be the costliest: 19,369 complaints with an adjusted loss of approximately $1.8 billion. Phishing scams were also prominent: 241,342 complaints, with adjusted losses of over $54 million.
Brand Impersonation Phone Calls and SMS
In addition to emails, cybercriminals often use voice calls or text messages-smishing to trick people. It is a very simple way to attract the target to some malicious websites with text messages. They send links to websites in their fake text messages which are often presented to people as sweepstakes, free gifts, or surveys with incentives. Once some unsuspecting people click on the link, it may lead to a fake login portal or a website with a drive-by download.
The consequences of victims falling to brand impersonation and other phishing scams can be severe, both for individuals and businesses:
1. Financial Loss: Fraudulent email communications can lead to unauthorized transactions, resulting in substantial financial losses for individuals and businesses.
2. Data Breaches: Brand impersonation can lead to data breaches, where sensitive information is compromised, such as personally identifiable information (PII), financial records, or intellectual property. This can result in identity theft, reputational damage, and legal implications.
3. Reputational Damage: Brands that are impersonated may suffer reputational harm as customers lose trust in their ability to secure their data, eroding brand loyalty and affecting long-term business viability.
4. Legal Consequences: Businesses that fail to adequately protect customer data or respond to brand impersonation incidents may face legal ramifications and regulatory penalties.
The harm caused by brand impersonation is not only to individuals but also to enterprises. Thus, to safeguard your business from exploitation by cybercriminals engaging in brand impersonation, it is crucial to implement specific measures that protect your digital identity.
Now that we know what brand impersonation is all about, let's explore how you can defend against this attack.
Secure Your Website with an SSL Certificate
For large companies and leading online businesses, an EV SSL certificate is the best choice. A company must go through an extensive process of authentication to get one EV SSL certificate which guarantees the highest level of brand trust and protection. This certificate records key information about your website and the domain it protects. The EV SSL certificate can also directly display the company name on the certificate, which not only enhances user trust but also effectively prevents phishing and hijacking.
Use an Email Signing Certificate
We already know that brand impersonation usually attacks in the form of emails, so we can use email signing certificates to ensure the authenticity and integrity of our emails. NicSRS's email signing certificate (S/MIME certificate) digitally signs and encrypts emails and attachments, which ensures the confidentiality and security of emails to a great extent. It can effectively prevent email phishing, email tampering, email leakage and other problems.
Show Your Identity with a Verified Mark Certificate (VMC)
VMC is a digital certificate used to verify trademark ownership. VMC enables email clients to display a logo next to the "From" field. Therefore, the recipient can see the logo of the sender's company before viewing the email, which makes the recipient confident that the email comes from a legitimate brand, helping to protect corporate customers and brands from phishing and fraud attacks.
Robust Authentication Measures
Implement advanced email authentication protocols such as SPF (Sender Policy Framework), DKIM (Domain Keys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) to verify the authenticity of incoming email messages and prevent spoofing.
In addition to using the above-mentioned specific tools or certificates to ensure that you are not attacked by brand impersonation, we can also start from the following aspects.
Employee Education
Regularly train employees on identifying phishing attempts, raise awareness about common tactics used in brand impersonation attacks, and emphasize the importance of verifying the legitimacy of email communications.
User Awareness
Encourage users to scrutinize emails carefully, paying attention to email addresses, grammar and spelling errors, unusual requests, and unexpected attachments or links. Remind them not to share sensitive information or click on suspicious links without verifying the sender's authenticity.
Regular Security Updates
Keep all software, including email clients, up to date with the latest security patches and updates. This helps protect against known vulnerabilities that attackers could exploit.
Brand impersonation through email poses a significant threat to individuals and organizations, potentially leading to financial loss, data breaches, reputational damage, and legal consequences. Remember, caution and skepticism are key when dealing with email messages, especially those claiming urgency or requiring sensitive information. By remaining vigilant and implementing effective security measures, individuals and businesses can protect themselves from the detrimental effects of brand impersonation through email.
As a leading digital certificate provider, NicSRS provides customers with better extended validation (EV) SSL/TLS certificates and S/MIME certificates to ensure the digital identity security of websites. If you have any questions, please feel free to contact us and we will provide you with timely professional help.
RELATED
2025-12-17 18:03:54
2025-12-04 11:44:39
2025-11-27 13:34:03
2025-10-22 15:01:21
2025-10-16 11:03:19
Categories

Free SSL Tools
Top Posts
Comments