SSL Certificate
Deploy an SSL certificate to enable HTTPS encryption of websites, trusted identity authentication and prevent against data leaks or tampering during transmission.
Get SSL Certificate >Blog > What Are Malicious URLs and How to Avoid Them?
Tag:
Malicious URLs
Digital Certificates
S/MIME certificates
4368:0
CatherineAugust 23 2023
As the digital world continues to evolve, individuals and businesses rely heavily on the internet for various activities, from communication and shopping to banking and entertainment. However, this digital dependence has also given rise to cybercrime that exploits vulnerabilities to carry out nefarious activities. Malicious URL (Uniform Resource Locator) is one of the common means used to launch attacks such as phishing, malware distribution, and identity theft. So what is malicious URL and how do cybercriminals use these dangerous links to their advantage? In this article, we will have a close look at the most common malicious URL tricks and defenses against them.
A Uniform Resource Locator (URL) is a reference or address that specifies the location of a resource on the internet. It's the string of characters that you enter into a web browser to access a webpage. A malicious URL, on the other hand, is a URL that has been crafted with malicious intent, aiming to deceive users and exploit their devices or data. These URLs usually lead you to download ransomware, viruses, or any other type of malware. Some can even lead you to provide sensitive information in order to steal company data, etc. Cybercriminals use malicious URLs to:
- Conduct phishing attacks. Malicious URLs are a staple of phishing campaigns. These URLs lead to fake websites designed to steal sensitive information such as login credentials, credit card numbers, or personal data.
- Trick users into downloading malware. When users visit compromised websites, malicious code is automatically executed without their knowledge, exploiting vulnerabilities in their browser or software to infect their device.
- Spread malicious content. Malicious URLs are used to spread false information, propaganda, or malicious content. Attackers leverage social media and messaging platforms to amplify their reach.
Fake file attachment
A common malicious URL is the use of fake file attachments. Attackers insert images that look like attachments into emails, prompting users to click them. These attachments are actually images that point to other malicious websites or software. The following are examples.
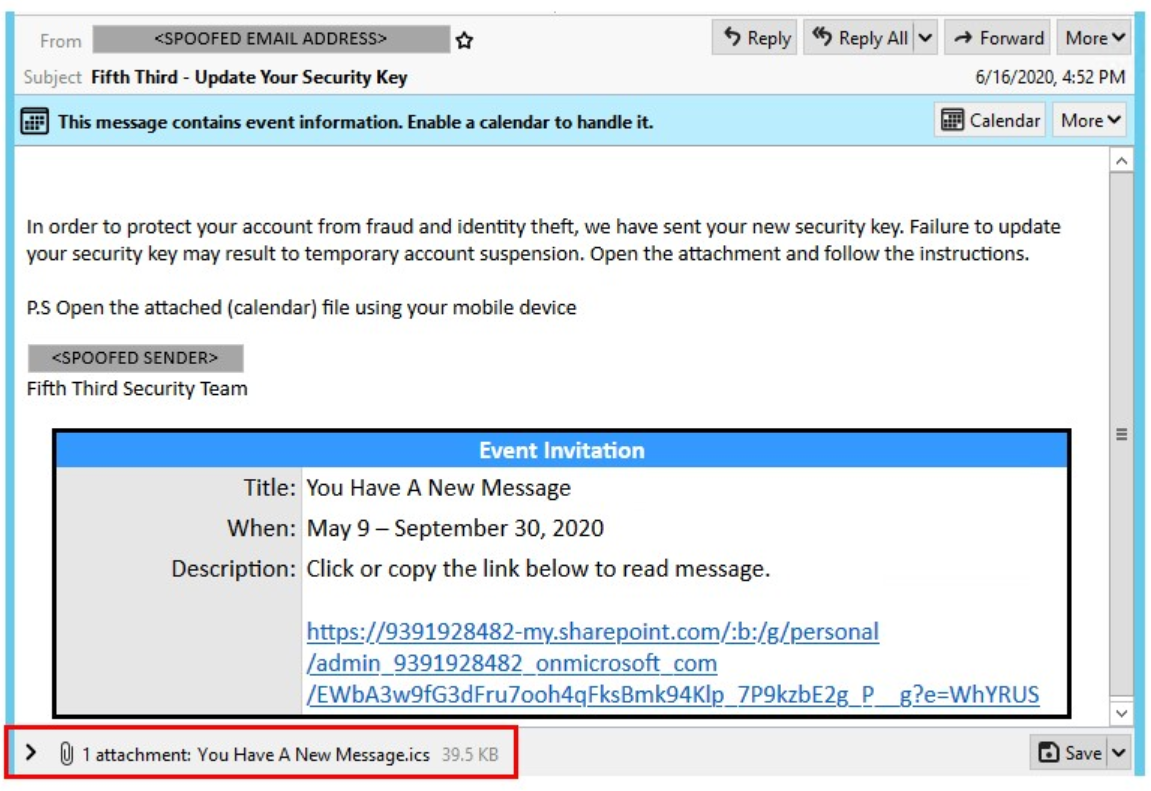
Domain mismatch
Hovering over the URL will display its full link. If the domain displayed in the URL does not match the domain you searched for previously, please do not click. This is most likely a phishing or malicious URL.
Malicious redirection
Some legitimate websites may contain malicious code injected by hackers. When users visit these websites and click on the target URL, they are redirected to harmful websites. In this situation, users will hardly realize that the URL they're clicking on are problematic unless they carefully verify them.
URL shortening
URL shortening services are often used to obscure the actual destination of a link. Attackers use these services to create short, seemingly harmless URLs that lead to malicious content. Users are less likely to recognize the threat when they can't see the full URL.
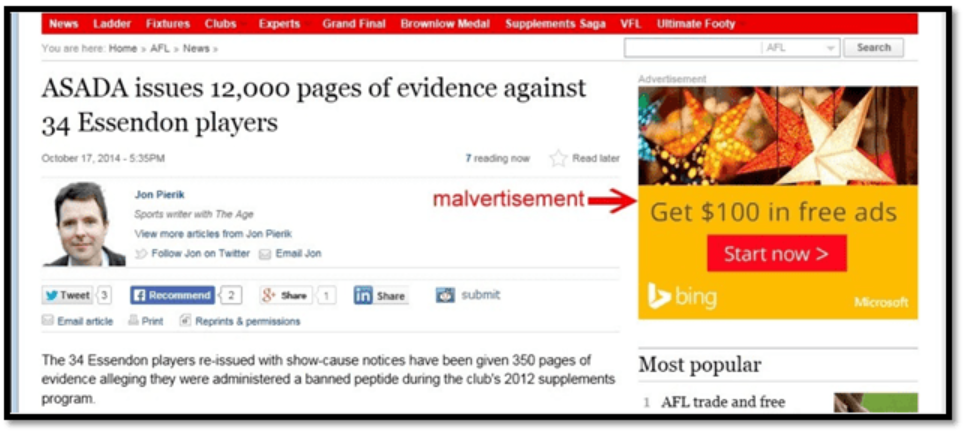
Malvertising URLs
Malvertising involves using malicious advertisements that lead users to harmful websites. These ads can appear on legitimate websites, and when clicked, they redirect users to malicious URLs that can distribute malware or engage in other malicious activities.
Rogue digital certificates
Most people think that as long as a website is equipped with a digital certificate, it must be a safe and trustworthy website. But this is not the case. Digital certificates can be issued to the wrong party, especially DV SSL certificates that only validate domain ownership.
Avoiding malicious URLs is crucial for both individuals and enterprises to maintain online security and protect sensitive data.
1. Be Cautious with Emails: Avoid clicking on links or downloading attachments from unknown or unsolicited emails. Even if an email appears to be from a trusted source, verify its authenticity before taking action.
2. Check Domain Names: Carefully examine the domain name for misspellings, extra characters, or slight variations from legitimate websites. Attackers often use similar-looking domains to deceive users.
3. View certificate details: Merely checking if a website utilizes an SSL certificate does not guarantee its security. Free SSL certificates can only offer basic encryption protection and are incapable of providing more robust encryption algorithms and advanced security features. In terms of security, DV SSL certificates are also not the optimal choice, as they only require domain ownership validation.
4. Don't click on pop-ups: Avoid clicking on pop-up ads or messages that claim your system is infected and prompt you to click on a link to fix it. Legitimate alerts usually come from your security software.
1. Use S/MIME certificates: Some phishers may infiltrate company employees' email accounts and take control. This way, the emails they send will appear to come from legitimate accounts. Email signing is enabled by importing and installing the S/MIME certificate into the email client. S/MIME certificates will effectively verify the true identity of the sender, thereby thwarting phishing attempts.
2. OV and EV SSL certificates ensure higher level of encryption and protection for websites. Since OV and EV SSL certificates require identity verification of the business that owns the URL, they are more difficult for phishing sites to obtain.
3. Train employee awareness: Learn about common phishing techniques and signs of malicious URLs. Additionally, instruct employees on how to report suspicious emails and websites to the IT team. Understanding these strategies can assist employees in recognizing and avoiding them.
4. Regular Audits: Conduct regular audits of security controls, network traffic, and user behavior to identify and address any unusual or suspicious activity.
The prevalence of malicious URLs highlights the ever-present need for vigilance and digital literacy in today's interconnected world. Malicious URLs serve as powerful medium for cybercriminals to exploit human trust, compromise systems, and steal sensitive information. As technology evolves, so do the tactics employed by these malicious actors. Vigilance, user education, and cybersecurity practices are essential to avoid falling victim to these threats.
RELATED
2026-01-28 17:44:18
2026-01-28 11:58:43
2025-12-18 15:37:42
2025-12-17 18:03:54
2025-12-04 11:44:39
Categories

Free SSL Tools
Top Posts
Comments